#OS
root@v12347:~# uname -a
Linux v12347.ovh.net 2.6.32.2-xxxx-grs-ipv4-64 #1 SMP Tue Dec 29 14:41:12 UTC 2009 x86_64 GNU/Linux
#HDD
root@v12347:~# df
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/sda1 5201532 673584 4265808 14% /
tmpfs 1026496 0 1026496 0% /lib/init/rw
udev 10240 2652 7588 26% /dev
tmpfs 1026496 0 1026496 0% /dev/shm
root@v12347:~# hdparm -t /dev/sda1
/dev/sda1:
Timing buffered disk reads: 126 MB in 3.03 seconds = 41.62 MB/sec
root@v12347:~# hdparm -T /dev/sda1
/dev/sda1:
Timing cached reads: 7326 MB in 2.00 seconds = 3664.46 MB/sec
#CPU
root@v12347:~# cat /proc/cpuinfo
processor : 0
vendor_id : GenuineIntel
cpu family : 6
model : 26
model name : Intel(R) Xeon(R) CPU E5504 @ 2.00GHz
stepping : 5
cpu MHz : 1995.001
cache size : 4096 KB
fpu : yes
fpu_exception : yes
cpuid level : 11
wp : yes
flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss syscall nx rdtscp lm constant_tsc up arch_perfmon pebs bts rep_good xtopology tsc_reliable nonstop_tsc aperfmperf pni ssse3 cx16 sse4_1 sse4_2 popcnt hypervisor lahf_lm
bogomips : 3990.00
clflush size : 64
cache_alignment : 64
address sizes : 40 bits physical, 48 bits virtual
power management:
root@v12347:~# tiobench --size 384
Run #1: /usr/bin/tiotest -t 8 -f 48 -r 500 -b 4096 -d . -TTT
Unit information
================
File size = megabytes
Blk Size = bytes
Rate = megabytes per second
CPU% = percentage of CPU used during the test
Latency = milliseconds
Lat% = percent of requests that took longer than X seconds
CPU Eff = Rate divided by CPU% - throughput per cpu load
Sequential Reads
File Blk Num Avg Maximum Lat% Lat% CPU
Identifier Size Size Thr Rate (CPU%) Latency Latency >2s >10s Eff
---------------------------- ------ ----- --- ------ ------ --------- ----------- -------- -------- -----
2.6.32.2-xxxx-grs-ipv4-64 384 4096 1 ###### 102.2% 0.001 0.14 0.00000 0.00000 2909
2.6.32.2-xxxx-grs-ipv4-64 384 4096 2 ###### 194.6% 0.002 8.38 0.00000 0.00000 1574
2.6.32.2-xxxx-grs-ipv4-64 384 4096 4 ###### 385.0% 0.005 20.04 0.00000 0.00000 727
2.6.32.2-xxxx-grs-ipv4-64 384 4096 8 ###### 413.6% 0.008 32.05 0.00000 0.00000 774
Random Reads
File Blk Num Avg Maximum Lat% Lat% CPU
Identifier Size Size Thr Rate (CPU%) Latency Latency >2s >10s Eff
---------------------------- ------ ----- --- ------ ------ --------- ----------- -------- -------- -----
2.6.32.2-xxxx-grs-ipv4-64 384 4096 1 ###### 129.6% 0.001 0.03 0.00000 0.00000 1953
2.6.32.2-xxxx-grs-ipv4-64 384 4096 2 ###### 67.56% 0.001 0.04 0.00000 0.00000 3906
2.6.32.2-xxxx-grs-ipv4-64 384 4096 4 ###### 123.8% 0.002 3.41 0.00000 0.00000 1953
2.6.32.2-xxxx-grs-ipv4-64 384 4096 8 ###### 56.57% 0.001 0.04 0.00000 0.00000 3906
Sequential Writes
File Blk Num Avg Maximum Lat% Lat% CPU
Identifier Size Size Thr Rate (CPU%) Latency Latency >2s >10s Eff
---------------------------- ------ ----- --- ------ ------ --------- ----------- -------- -------- -----
2.6.32.2-xxxx-grs-ipv4-64 384 4096 1 39.91 11.80% 0.021 421.55 0.00000 0.00000 338
2.6.32.2-xxxx-grs-ipv4-64 384 4096 2 30.80 29.35% 0.061 2149.02 0.00203 0.00000 105
2.6.32.2-xxxx-grs-ipv4-64 384 4096 4 29.44 52.49% 0.112 2117.31 0.00407 0.00000 56
2.6.32.2-xxxx-grs-ipv4-64 384 4096 8 34.61 50.22% 0.163 5115.43 0.00203 0.00000 69
Random Writes
File Blk Num Avg Maximum Lat% Lat% CPU
Identifier Size Size Thr Rate (CPU%) Latency Latency >2s >10s Eff
---------------------------- ------ ----- --- ------ ------ --------- ----------- -------- -------- -----
2.6.32.2-xxxx-grs-ipv4-64 384 4096 1 16.75 2.572% 0.005 1.64 0.00000 0.00000 651
2.6.32.2-xxxx-grs-ipv4-64 384 4096 2 44.54 9.122% 0.005 4.06 0.00000 0.00000 488
2.6.32.2-xxxx-grs-ipv4-64 384 4096 4 40.43 18.63% 0.007 10.73 0.00000 0.00000 217
2.6.32.2-xxxx-grs-ipv4-64 384 4096 8 18.86 -13.5% 0.003 0.63 0.00000 0.00000 -140
# RAM
Not tested.
# NETWORK (not really representative)
# using iperf from a RPS limited to 100Mbit/s
[ 3] 0.0-10.0 sec 113 MBytes 94.7 Mbits/sec
# ideally I would have to rent another minicloud to check the effective performance (because I guess it is limited by my RPS). I guess result would be closer to 10Gb/s or 1Gb/s




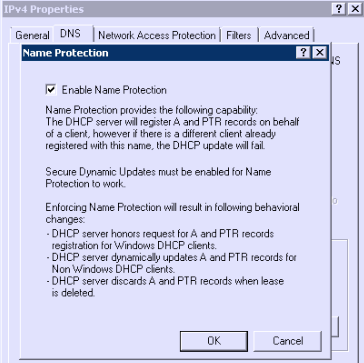






 - then validate
- then validate



 Since its a service, we have to choose a user account for running it. This permits controlling very precisely the permissions the rsync user will be granted.
Since its a service, we have to choose a user account for running it. This permits controlling very precisely the permissions the rsync user will be granted.